How I could've accessed personal details of tens of thousands of people

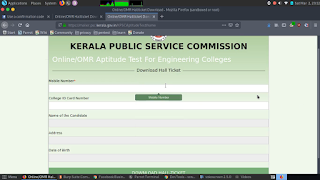
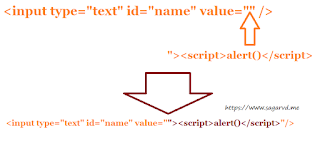
This is a security issue I found in one of the company that work in different fields. They make different type of electronic equipments as well as offers the public an easy way to enroll and avail benefits of different Govt Schemes. Let's say the company name is XYZ and the domain is xyz.com. They provide people a way to enroll to various govt services with their service centres, like a govt agency and public can register/ apply for any kind of govt services, schemes, etc. They're also an authorized service provider of a Govt Scheme by a state govt. I was checking the functionalities in their website and noticed a login url under /admin . I visited /admin/login.php and saw a Login page. I tried 5-10 different user:pass combinations and none of them worked. I then decided to try sqli in the login form. Like most of the PHP sites created by noooobs, this site is also vulnerable to sqli in login form. I got access to the admin panel, I saw scanned copies of ID c